What is VPN, How Virtual Private Network works Explained

VPN stands for Virtual Private Network, hides your IP address, and encrypts the data that you are sending or receiving via your internet connection so that we can make secure communication on the open internet. Or we can say VPN hides your browsing activity and protects your data from hackers. Also using VPN can unblock Geo-restricted websites, securely download from torrent, unblock US Netflix, and more. Again If you are on public wifi using VPN keep safe your online activity safe from third-party eyes.
If you want to access your office network from your home, then you can work securely on the Internet by connecting your computer to your company’s VPN server first. VPNs essentially forward all your network traffic to the network, which is where the advantage lies – such as remotely accessing local network resources and bypassing Internet censorship. Most operating systems have VPN support integrated.
What is VPN?
The VPN creates an encrypted (intelligence) connection from the device to the network to the Internet. The job of an encrypted connection is to protect the personal data of the user. This prevents your personal information from being hacked by the hacker and helps you to work in a secure manner. VPN technology is used for corporate companies, government websites, educational institutes, or personal use.
Think if you are in China and want to play YouTube on your computer or mobile, then you will need a VPN for this, then we can watch YouTube while sitting in China.
How does Virtual Private Network (VPN) work?
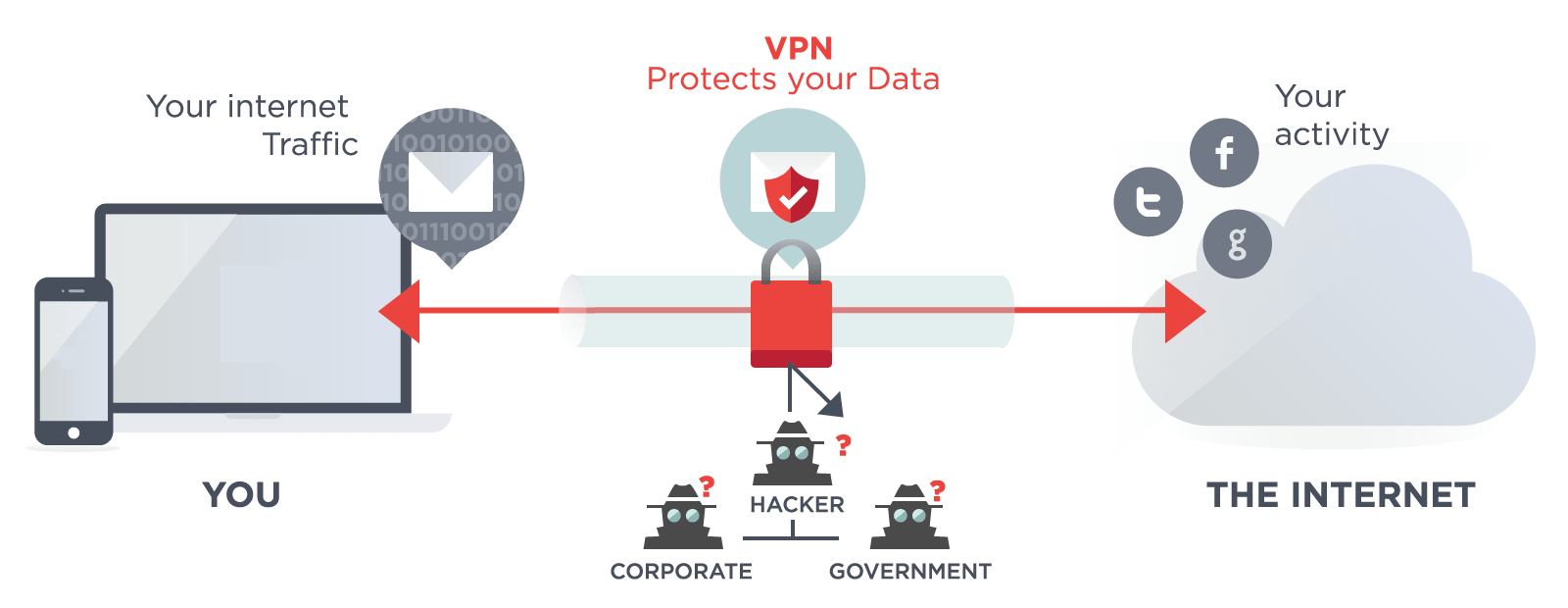
A VPN works by routing your device’s Internet connection through your chosen VPN’s private server (Secure Tunel) instead of your internet service provider (ISP) so that when your data is transmitted to the internet, it comes from the VPN rather than your computer. A virtual private network protects your connection and all data that passes through that connection in three layers:
1st layer → Encryption. Before anything else, your VPN encrypts your data (or converts all the information into a code that can’t be unencrypted without a matching key). So even if an unauthorized person manages to get ahold of your data, they still won’t be able to understand it.
2nd layer → Tunneling Protocol. Your VPN then establishes a direct connection between your computer and a VPN server. This private “tunnel” secures your connection over the public internet.
3rd layer → Authentication. Only users with the right authentication keys can access the tunnel and the VPN server. This is also the protocol that un-encrypts your data after it reaches its destination.
A VPN creates a private “tunnel” from your device to the Internet and hides your important data through something known as encryption.
What are VPN protocols?
A VPN protocol is basically the technology that uses your VPN service to ensure that you get the fastest and most secure connection to the Internet. Combining encryption standards and transmission protocols, a VPN protocol determines how your data is transmitted between your device and a VPN server. The main VPN protocols in use today are:
Point-to-Point Tunneling Protocol (PPTP)
Created by Microsoft, it is one of the oldest protocols used on the Internet today. In this way, it is really only useful when you are using it on older Windows operating systems, although it is faster and easier to deploy. However, if a VPN service provides just this, then it is not recommended.
Layer 2 Tunneling Protocol (L2TP / IPSec)
This protocol is a combination of the PPTP and L2F protocols already mentioned by the networking company, CISCO Systems. This makes data tunneling more secure than PPTP but does not actually have encryption or privacy capabilities. As such, it is often bundled with IPSec, which is a secure protocol.
Secure Socket Tunneling Protocol (SSTP)
Another VPN created by Microsoft, it is a VPN equivalent to the protocol used by websites for encryption purposes. A very secure protocol, only two parties involved in the transmission of data can decode it.
Internet Key Exchange, version 2 (IKEv2)
A new, more secure version of L2TP, IKEv2 was also developed in collaboration between Microsoft and Cisco. Like the predecessor, it is often combined with IPSec. This protocol is particularly effective on mobile devices.
Openvpn
Open VPN is an open-source VPN technology and is widely viewed as the best. The term “open source” means that countless developers are constantly improving the technology, and anyone can use it and modify it for their needs, be it individuals or companies.
Its effectiveness has been put to the test several times through high-profile audits. OpenVPN is one of the most popular protocols and is considered the most secure, providing security similar to the protocols mentioned earlier, but more extensively.
Before taking a VPN, it is a good idea to see what protocols they provide and what will happen if you are using their VPN.
Why do people use VPNs?
Many VPNs will work directly with an operating system’s settings – such as Windows, Mac OS, iOS, or Android – so that every app that connects to the Internet – such as a browser, banking, or social media app – is protected.
Standalone VPN Service
This VPN is most commonly used by households and small businesses, it uses an application that creates an encrypted connection to a private network that you can use to connect to the Internet at large.
Browser Extensions
Some VPNs act as a browser add-on. There are a plethora of add-ons that you can install in a browser like Google Chrome or Firefox, while Opera comes with an inbuilt VPN. The downside to this is that your data will be protected only when you are exclusively using that browser. Other apps will not be safe. In addition, browser VPNs are slightly more vulnerable and may cause IP leaks.
If you decide to opt for a browser add-on or extension, it is best to take it from reputable companies offering other VPN services. There are a lot of shady browser add-ons, scammy, read reviews from a data harvester and always read the fine print of terms of service.
Router VPN
Another way to implement VPN is through a VPN-enabled router. This is ideal if you have multiple devices that you want to protect as it will protect every device connected to the router, saving you to install VPN individually. Also, you only have to sign in once; Your router will always be connected to your VPN.
Connecting your router to a VPN is not as difficult as you might think. First, you have to sign up for a VPN service, then you will need a router. The most convenient router to obtain is the one that is designed to give instant support to the VPN, these routers may be slightly more expensive than regular routers, but the convenience is worth it.
Corporate VPN (Corporate VPN)
Corporations often use remote-access VPNs for employees who work remotely. Through this VPN employees can securely access the company’s personal intranet, often using passwords and apps. It is a custom-made solution that requires personalized development and heavy IT resources.
Why do people use VPNs?
People use VPNs for countless reasons. Some of these reasons are specific, while some people have VPN as another layer of security in addition to a good antivirus program and typically have sensible Internet access.
As mentioned earlier, a common reason for using a VPN is to protect your online activity while you are on public Wi-Fi hotspots.
Another reason for using VPNs is to gain access to Region restricted content, whether it is a TV show on Netflix in your country, or around the Internet censorship laws of a certain jurisdiction.
Ultimately, online anonymity is high for why people use VPNs. In these days where public data is being used in shady ways has become a daily occurrence, keeping private information private is more important than ever.
Keep in mind some important things while taking VPN
Hopefully, now you have a better idea of how VPN works. Here is a list of things to look at before choosing a VPN:
Is it free or Paid? – When it comes to safe, fast service, paying for a VPN is really worth it. Many free VPNs only offer the PPTP protocol which, as we said earlier, is not really very effective these days. They have less server space and less bandwidth to offer. Many times with these free options your data is tracked and sold to third-party businesses. Paid VPN options are more often than not their more powerful counterparts with more powerful security protocols on offer. A paid VPN should have more server space and more bandwidth, which gives you a faster service. If you get stuck in any issue then they also have customer support.
- Are VPNs legal in your jurisdiction?
- Where is the VPN server located?
- Does the VPN company log your activity?
- Does it protect your entire device or is it just an add-on?
- What are the protocols of the VPN encryption mechanism?
The VPN service has the number of servers and the amount of bandwidth – if both are low it can make for a very slow web-surfing experience.
